Sessions
Sessions form a history of users opening your phishing links, with recorded credentials and captured session cookies.
Once users open your phishing lure link, a new phishing session will be created for them to track the progress of the phishing attempt. When they send their credentials over the tracked parameters, these credentials will be stored.
You can list the history of all logged phishing sessions with:
: sessions
On the list you will be able to see the phishlet, which was used for the phishing session, logged credentials, originating IP address of the person opening the phishing link and date & time when the link was opened.
You can see a more detailed view of any recorded session with:
: sessions <id>
In this view you will also be able to see the captured session cookies in JSON format, which you can copy and import in your web browser to impersonate a captured user session.
tip
Most of the time when you import captured session cookies into your browser, you will not be asked for valid username and password. Website will act as if you were already logged in.
If you want to delete any recorded session you can type:
: sessions delete <id>
And to delete all recorded sessions:
: sessions delete all
Impersonating sessions
In order to be able to impersonate a captured user session you will need an extension for your browser, which will allow you to import session cookies in JSON format.
For Chrome you need EditThisCookie or Cookie-Editor and for Firefox there is its own version of Cookie-Editor
It is most important that you clear all of your browser cookies before importing captured session cookies. You should create a dedicated profile in your browser just for session impersonation.
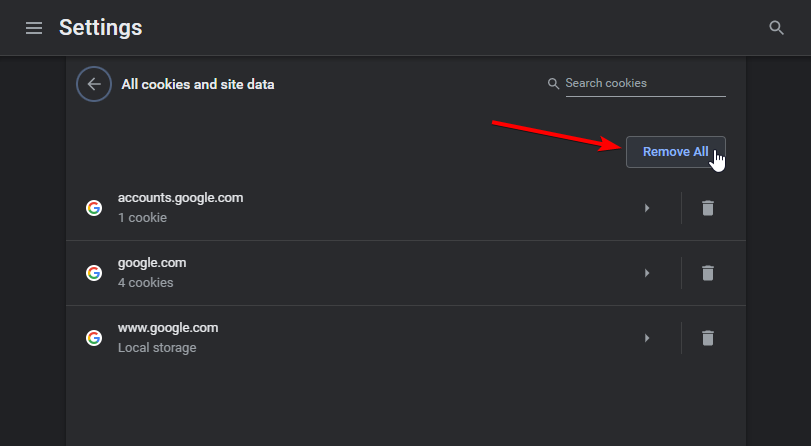
If you're on Chrome, navigate to chrome://settings/siteData URL and press the Remove All button to purge all cookies from browser's profile storage:
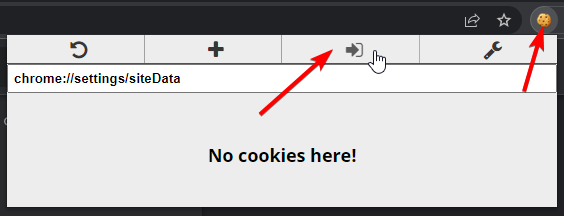
When you're ready to import captured session cookies, click the cookie editor extension icon and press the Import button:
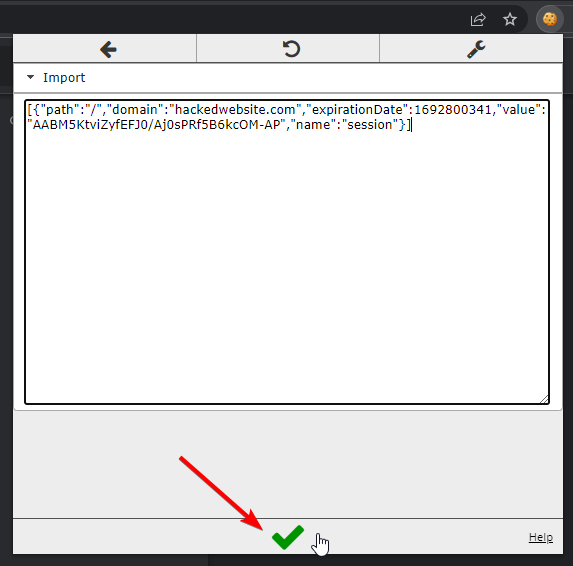
Then copy the captured cookies JSON from Evilginx terminal, paste it into the import window and click the confirmation button.
And you're done! Now when you open the website, which the session cookies were for and you should be logged in, while impersonating the phished user.
Commands
: help sessions
sessions
Shows all captured credentials and authentication tokens. Allows to
view full history of visits and delete logged sessions.
sessions
show history of all logged visits and captured credentials
sessions <id>
show session details, including captured authentication tokens, if available
sessions delete <id>
delete logged session with <id> (ranges with separators are allowed e.g. 1-7,10-12,15-25)
sessions delete all
delete all logged sessions